Secure Private Access
THE CHALLENGE – NETWORK-CENTRIC SECURITY
Enterprises are in the midst of a massive technology shift. Internal applications that were once hosted in the data center, running on an internal network protected by a DMZ, are now moving to the public cloud.
For 30 years, enterprises have relied on network-centric methods to connect users to the network, and by extension the applications running on it. But the way users work has changed, and with applications moving to cloud, the perimeter has extended to the internet. This renders network-centric solutions, like remote access VPNs, obsolete.
TRADITIONAL DMZ IS NO LONGER EFFECTIVE IN THE CLOUD ERA
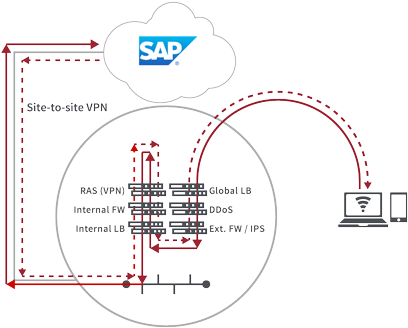
The traditional DMZ approach worked well for data center applications. It provided an additional layer of security for the internal LAN, allowing IT to expose only external facing services to the internet and place all other internal services behind a firewall. But with applications moving to cloud, the perimeter has been extended to the internet, which the DMZ was not built to secure.
Moving the DMZ to the cloud—often referred to as the “virtual DMZ”—is recommended by some cloud service providers, but it’s expensive, difficult to architect, and complex to implement. It starts with a traditional VPN gateway stack hosted in the data center, and requires architecting and implementing a virtual network (VNET) specific to each cloud provider (often involving NIC, additional network access variables, and more) and a VPN appliance to connect both the internal and virtual networks.
The complexity of this method slows the adoption of public cloud, drives up appliance-related costs, and frustrates users attempting to access public cloud applications.
WHY VPN AND NETWORK-CENTRIC APPROACHES FAIL
- Places users on-network, which increases risk
- Provides a poor end-user experience
- Inbound connections create opportunity for DDoS attacks
- Requires appliances, ACLs and FW policies
- No ability to provide application segmentation
- Lack of visibility into app-related activity
OUR SOLUTION – USER AND APPLICATION-CENTRIC SECURITY
Zscaler Private Access (ZPA) is a cloud service from which provides zero-trust, secure remote access to internal applications running on cloud infrastructure or on data center. ZPA provides seamless and secure access to internal applications, whether they are hosted in the data center or cloud.
ZPA delivers a software defined perimeter (SDP), a network security method that stemmed from work of the Defense Information Systems Agency (DISA) in 2007. As such, the service is a completely different network security method than the traditional DMZ. It provides zero-trust access to internal applications using software—on a need-to-know basis—by looking at two criteria: user device and user identity.
VPN vs. ZPA (Zscaler Private Access)
UNIQUE DESIGN BASED ON FOUR KEY TENETS
- Connect users to applications without placing users on the network
- Never expose applications to unauthorized users
- Enable app segmentation without network segmentation
- Provide secure remote access without using VPN appliances
ZPA provides a simple, secure, and effective way to access internal applications. Access is based on policies created by the IT admin within the Admin Portal and hosted within the Zscaler cloud. On each user device, a piece of software called Z-App is installed. Z-App ensures the user’s device posture and extends a secure micro-tunnel out to the Zscaler cloud when a user attempts to access an internal application.
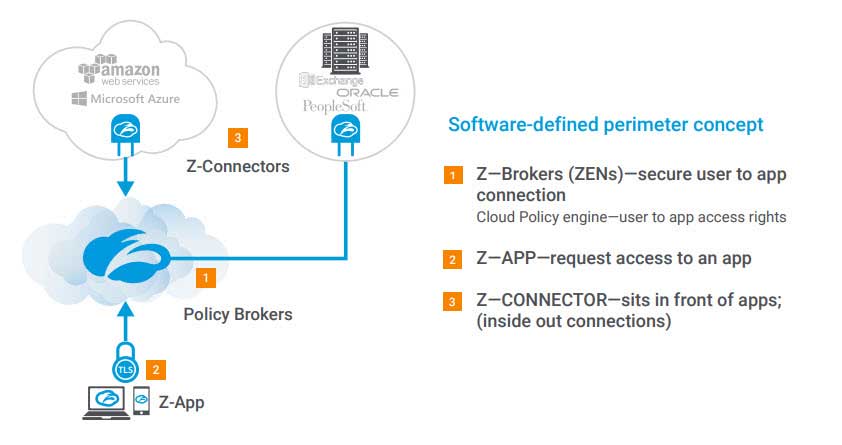
Adjacent to an application running in a public cloud or data center, ZPA places a small piece of software called Z-Connector, deployed as a VM, which is used to extend a micro-tunnel out to the Zscaler cloud. The Z-Connector establishes an outbound connection to the cloud, and does not receive any inbound connection requests, thereby preventing DDoS attacks. Within the Zscaler cloud, a Z-Broker approves access and stitches together the user-to-application connection.
ZPA is 100% software defined solution, so it requires no appliances and allows users to benefit from the cloud and mobility while maintaining the security of their applications.

EMPOWER YOUR ENTERPRISE WITH ZPA
- Standardize and control access to internal applications
- Reduce risk and exposure
- Gain visibility into the application environment
- Simplify remote access to the cloud
- Accelerate mergers and acquisitions
Want to hear more about our Secure Private Access Solution? Use the contact form, and we will contact you soon.


 DOWNLOAD SOLUTION BRIEF
DOWNLOAD SOLUTION BRIEF